That article on fried green tomato recipes made your mouth water. In fact, you started thinking about how they might solve some of the surplus from a good gardening season. The instructions for a couple of the dishes seemed like good side items to go with your late-summer barbecue this weekend. You’re about to forward the link to the article to your phone to use in the kitchen, but just as your cursor is hovering over the “Share” icon, you spot the “Print Recipe” button near the bottom of the page. It might be a waste of paper, but following recipes on the tine phone screen is just maddening.
Click.
Some kind of fine print…search engine…browser extension…yeah, whatever.
Confirm.
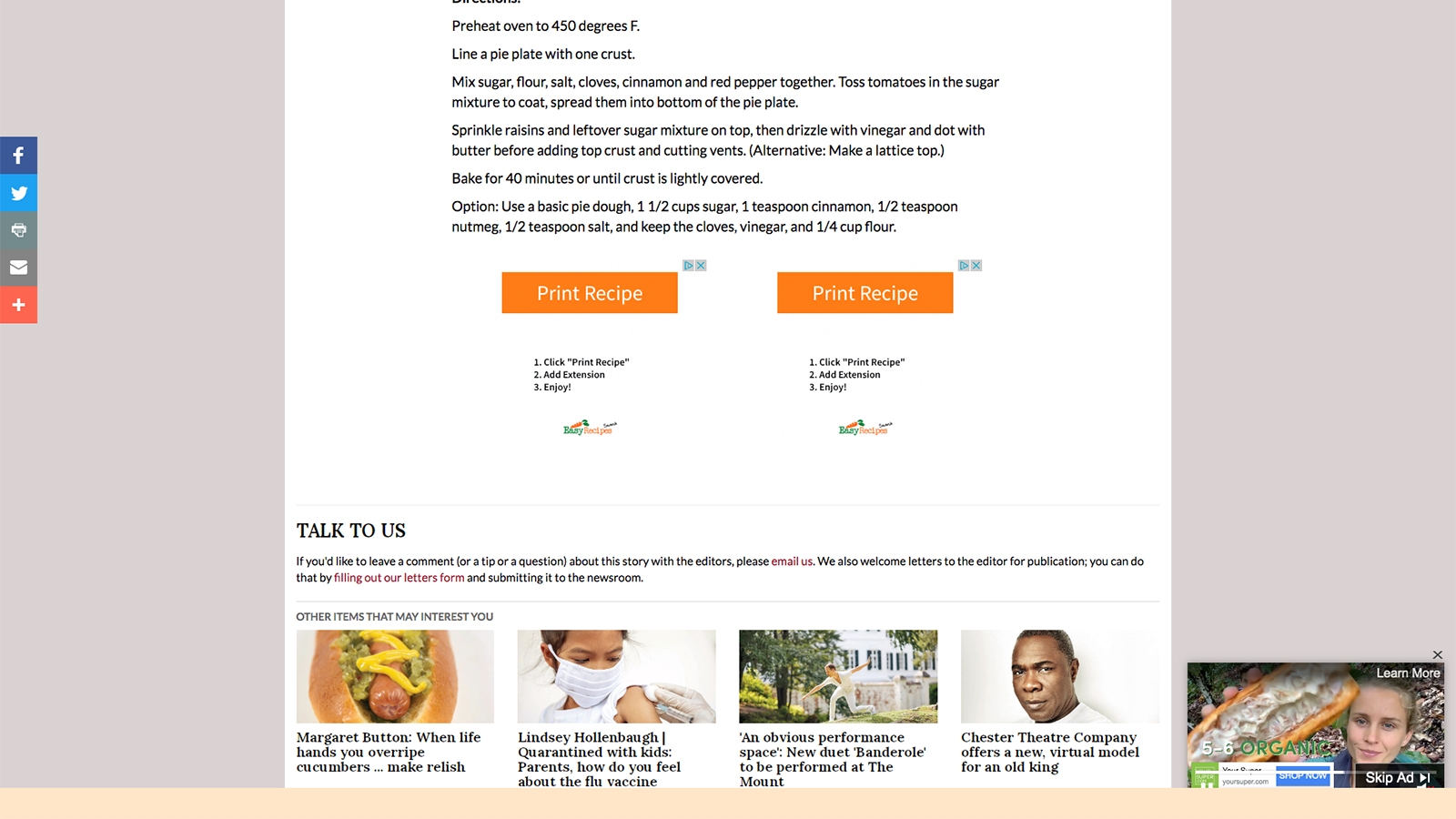
Except that it doesn’t bring up your familiar print dialogue box. In fact, you’re now looking at an unfamiliar search results page.
You’ve just been pwned. And now, now matter how you try, you can’t get back to your regular default search engine. In fact, even when you try to use this new search tool, the results look…dodgy.
And it may be worse than that. A lost worse.
You’ve just installed a malicious bit of software that’s hijacked your web browser. With no warning it will, at the very least, return cherry-picked search results that will earn the creator money when you click on them. In worst-case scenarios, this “malware” can harvest all your browsing data (pages you visited, passwords you entered, searches you performed) and siphon up personal information that could lead to identity theft.
We got in touch with Jason Rudd, founder and CEO of PCGuys, on Elm Street in Pittsfield, by phone. In addition to computer repair and custom computer builds, he and his team offer a range of services, including computer protection, data backup and recovery, and — you guessed it — virus and spyware removal. He described some of the telltale signs of malware infestation.
“Well, usually the first thing it does,” Rudd explained,” a lot of times, it’ll change your search — like your default would be Google? It’ll change it to something else, some weird name. Or automatically, if you click to go to JC Penney, it redirects you to a different site entirely. Usually, redirects or anything where it tries to get you to download something, or call a number — that’s a red flag right off the rip.”
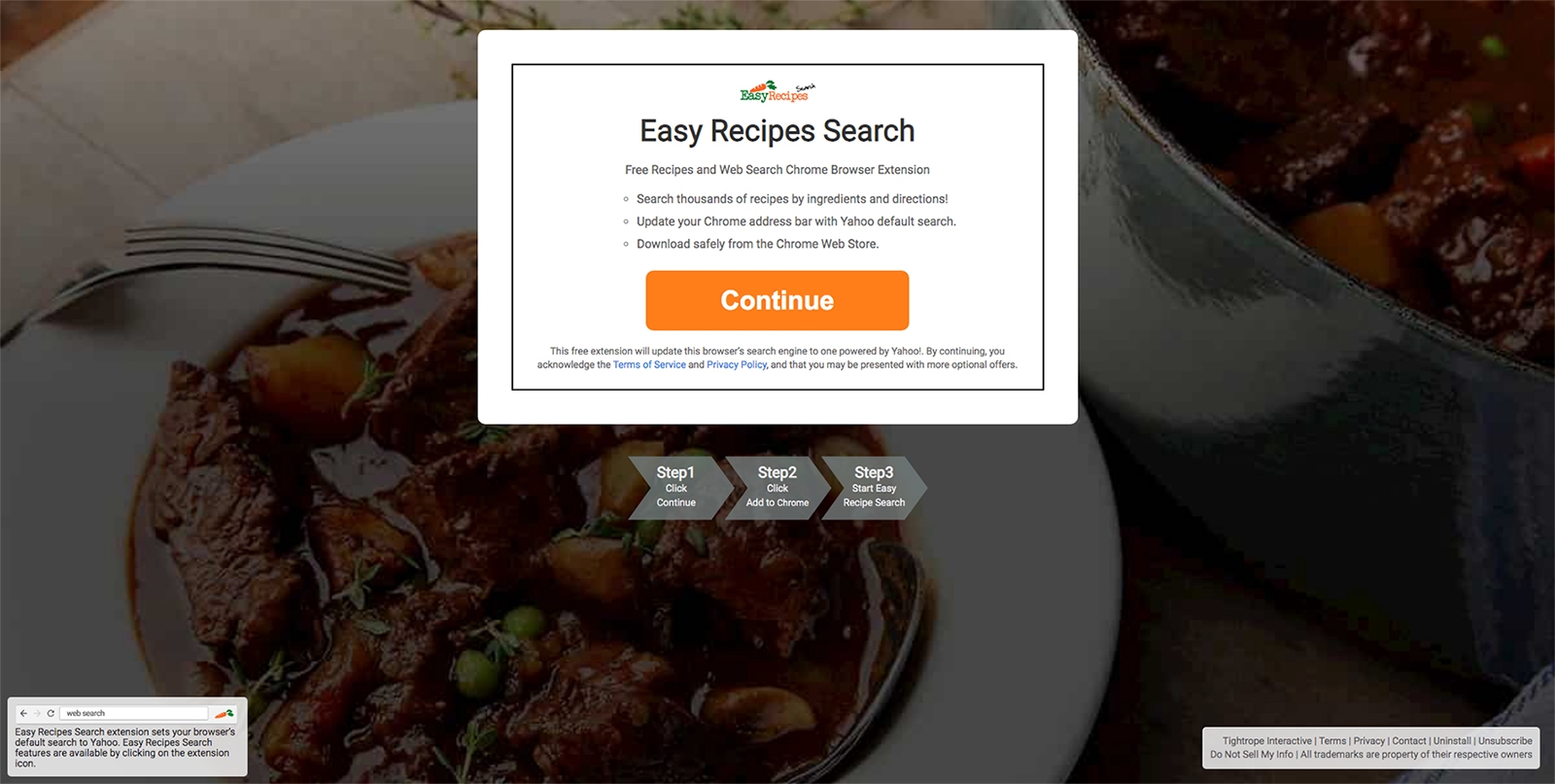
Malware Bytes is a software company that supplies consumers and businesses with utilities that scan for, and remove, threats that attack systems or data, introduce unwanted behaviors, and degrade performance. Since about 2008, the company has been an industry leader in preventing damage from just these kinds of threats. And they’ve seen the “Print Recipe” operation before. In fact, they identify exactly the malware you may have unintentionally installed.
“The Malwarebytes research team has determined that Easy Recipes Search is a search hijacker,” explains an entry in their support forum.” “These so-called “hijackers” manipulate your browser(s), for example to change your startpage or searchscopes, so that the affected browser visits their site or one of their choice.
Now, you begin searching the web for clues as to how this could possibly have happened. Good luck — some of these nefarious search extensions have been known to protect themselves by mysteriously failing to yield information about themselves. Downloading a different browser entirely, and searching for answers with an uninfected search tool, you’re able to finally get to the bottom of the situation. You learn that this potentially unwanted application (PUA — a deceptively mild euphemism for “I didn’t want this crap on my hard drive), is sneaked in through advertising designed to look like part of the article. When you clicked “Print” you were on your way to inadvertently exposing your computer, and personal information, to bad actors.
The website, PCrisk.com, details the dangers of this type of data ambush in no uncertain terms. They explain that, “browser hijackers often gather addresses of visited websites, entered search queries, geolocations, IP addresses, and other browsing data. In some cases, they also collect personal, sensitive information.
Rudd said the intrusion could represent a range of menaces. “I mean with malware,” he said, “it all depends on the person’s intent. It could be something where it’s ransomware — they could lock the computer, they could try to request money.”
PCrisk.com agrees, noting, “People who have such apps installed on their browsers and/or operating systems risk experiencing problems relating to privacy and browsing safety. There is also a possibility that gathered information will be misused to steal their identities.”
Affiliate Advertisement
The important thing, he cautioned, is not to try to negotiate with anyone or give in to their demands. “A lot of times customers and people who have come to our shop, they freak out,” he said. “Some people even let people on their machine, which is always not good. You never want to call the phone numbers. You never want to follow through with any of that kind of stuff on there.”
Then it occurs to you — that article was on the website of your trusted local newspaper!
Yes, sadly, newspaper publishers, even locally owned independent ones, are between the sword and the wall in terms of financial survival these days, and most have turned to a guaranteed money-maker: programmatic advertising. This type of ad sales is done mostly automatically, through a system that allows advertisers to upload their linked ad and publishers to create little boxes of advertising real estate in and around news articles. Depending on how you’ve set your browser’s privacy settings, these systems can also track your activity as you surf the web, learning about your interests and serving ads tailor-made to attract you.
The advertiser can choose what types of online publications can host the ads and what types of articles they should show up in. The publisher can choose what sorts of ads should not be shown in certain sections, or at all. Most of these ads are benign (although those awful clickbait “You might also like” stories are delivered through similar systems — skeezy, but mostly harmless). The publisher may earn revenue when a reader clicks on an ad or simply when an ad is displayed.
Local Service Spotlight
PC Guys
123 Elm Street
Unit 2 Pittsfield, MA 01201
“I’ve been doing this well over 10 years. I just didn’t open a storefront until probably two and a half years or so ago. At the time, it just wasn’t easy to locate a smaller space. I didn’t want to spend, you know, $3,000 a month on rent for a new business. We finally located a good space, and we’ve just been doing great ever since. Service wise, I mean, we offer computer pepair, cell phone repair. We do data recovery. We even do TV repair — TVs are basically just like computers just flat. So we offer a wide range of services here.”
But wait a minute! Does that mean that your local newspaper is getting paid to infect your computer with PUAs? Yes and no. Most of these programatic ad delivery systems are designed to catch sleazy advertisers and their invasive code. But there are millions and millions of these ads been placed every hour, and even the most dangerous malware operations can be disguised as a legitimate offer. Especially when the click-through takes you, not to the item you thought you were interested in, but a page asking you to confirm installation of software.
So, no, your local newspaper is probably not part of this shadowy bait and snatch. On the other hand, even though these ad placements are done automatically through algorithms, advertising sales managers, editors, and publishers arguably should be paying attention to the foreign content appearing on their pages within or next to actual articles — we repeatedly clicked “reload” on one recipe article and discovered that one or another of these recipe traps (yes, there’s more than one of them) appeared in one out of every seven page refreshes).
Now you’re pulling your hair out, wondering if there’s any way to restore your browser and sanity back to the way they were before you ever set eyes on that fried green tomato recipe. The good news is that removal is fairly simple and straightforward, whether you’re on a PC or Mac (or iOS or Android phone — yikes! Malware is showing up there, too!). We provide step-by-step directions for users of the Apple browser, Safari, but have no fear if you use Brave, or Firefox, or Chrome — you’ll find your solution below.
If you’re an Apple Safari user:
• Force Quit Safari ( command + option + esc keys).
• After Safari has successfully shut down, restart Safari holding the Shift key.
Problem didn’t go away?
• Empty Caches (Safari menu > Preferences > Privacy > Remove all website data. (If you don’t want to remove all your History, open Safari Preferences > Advanced and check mark “Show Develop Menu” then choose “Empty Caches” from Develop Menu ).
• Go to Safari Preferences > Extensions and look to see if any extensions exist. If so, delete it.
• Finally, in Safari Preferences > Search enter you preferred search engine.
If that still doesn’t cure what ails your rig, or if you’re on a PC, download and run the free Malwarebytes, one of the most trusted threat detection and removal tools in the industry. While it won’t cost you anything to use the tool, the available premium version provides ongoing protection that offer real peace of mind, considering how sketchy the internet still can be after all these years.
(Confession: we ran the free version of Malwarebytes, smugly thinking we’re way too cool to fall for any malware shenanigans…The scan turned up SIX.)
Rudd suggests that, in many cases, people can eliminate the infection without professional help. By installing legitimate virus protection software, computer users can usually stay bug-free. But not always.
“Most people buy the generic suites from McAfee and Norton, and they should handle that kind of stuff — a lot of those do have hijacking prevention. But sometimes stuff gets through, and then they have to come to us and we have to use our tools, our software to remove the stuff. It really just depends on what it is — if it’s a Trojan horse, what version of the virus it is, to determine what has to be done.
Going forward? Remember that even your trusted local newspaper’s online version may contain more than just “all the links that are fit to click.” Oh, and maybe buy a cheap used tablet just to use in the kitchen so you don’t have to waste paper printing recipes anymore.














You must be logged in to post a comment.